GSMA Call Check has been developed specifically to fight and overcome one of the most significant voice telephony fraud problems impacting consumers and operators alike: CLI spoofing
CLI spoofing assists fraudsters to conduct a wide range of activities; for instance, to disguise their identity as a means to facilitate scamming activities towards consumers, or simply to misrepresent traffic to gain commercial advantage.

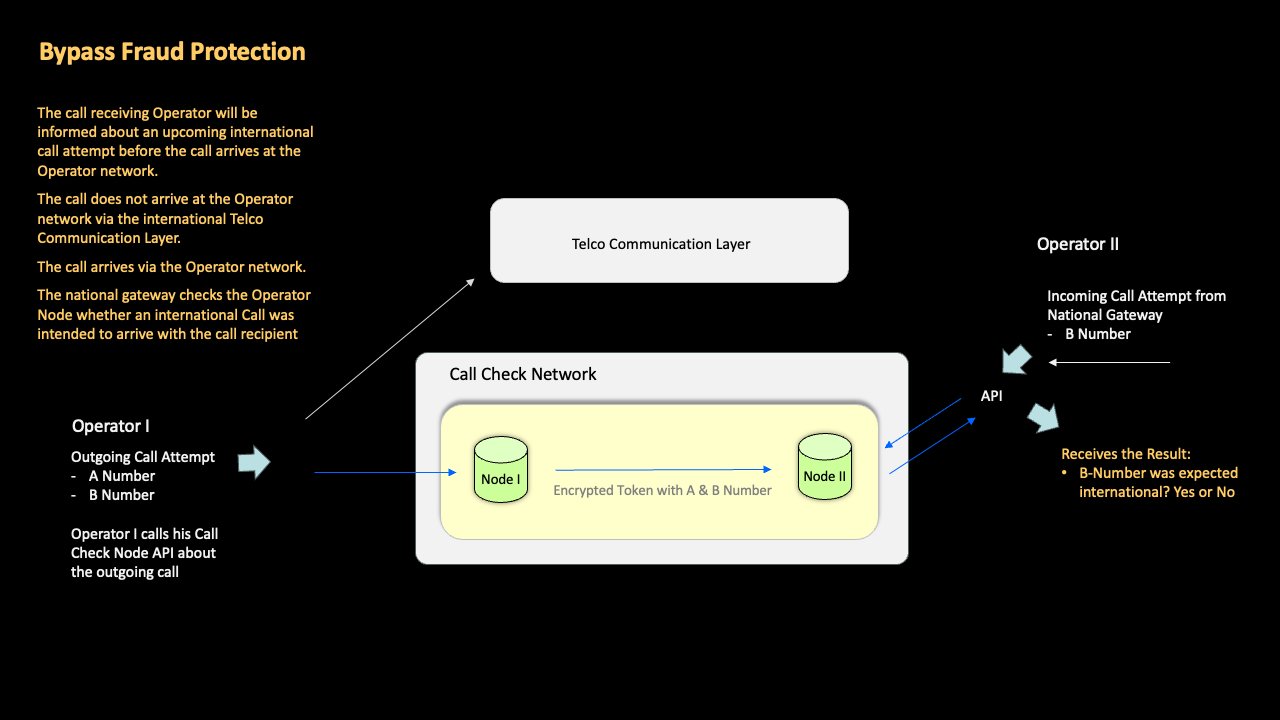
To prevent scam calls from reaching consumers, GSMA Call Check aligns with recent “zero trust” regulatory initiatives that mandate the blocking of international calls displaying a spoofed national CLI, but crucially with the ability also to support the safe passage of valid traffic scenarios (e.g., roaming subscribers) that are identified as legitimate exceptions in such policies.
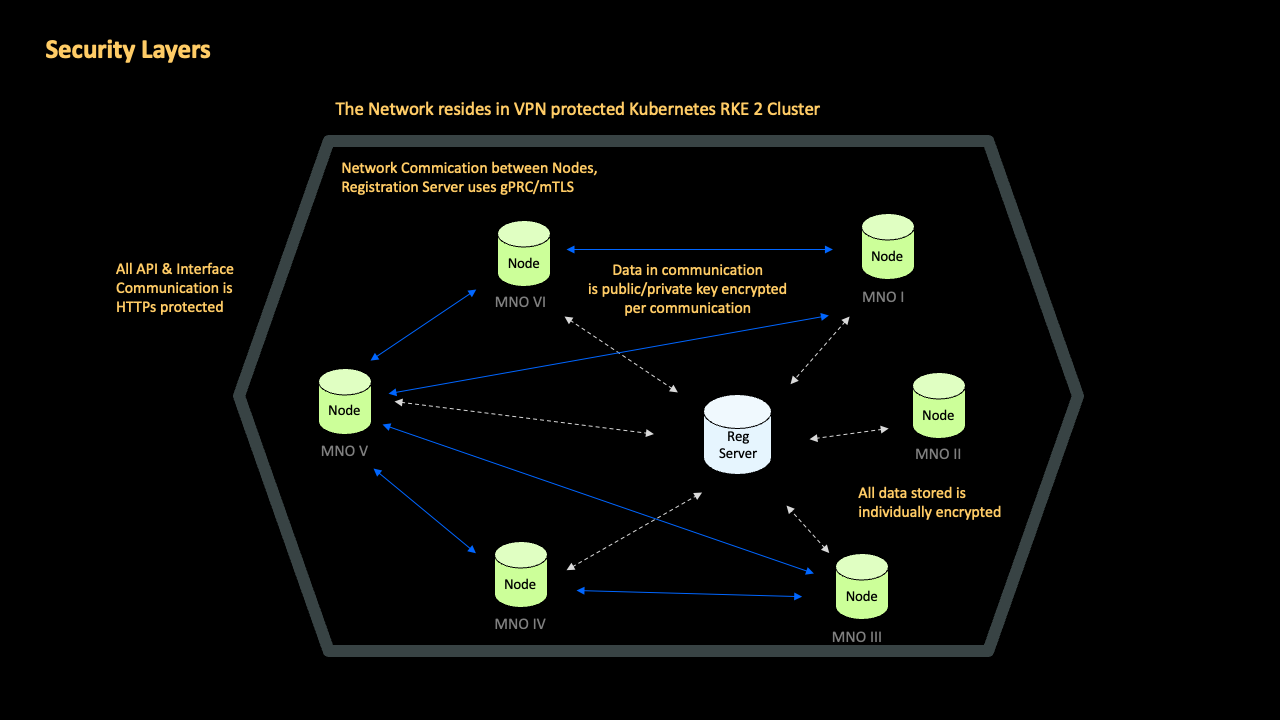
GSMA Call Check addresses this by introducing an additional communication flow (a security network) that runs in parallel to and indeed faster than the regular telephony network. In essence it is a highly secure, peer-to-peer, collaborative operator network, operating automatically in realtime, and delivered by GSMA as a secure and encrypted hosted service.
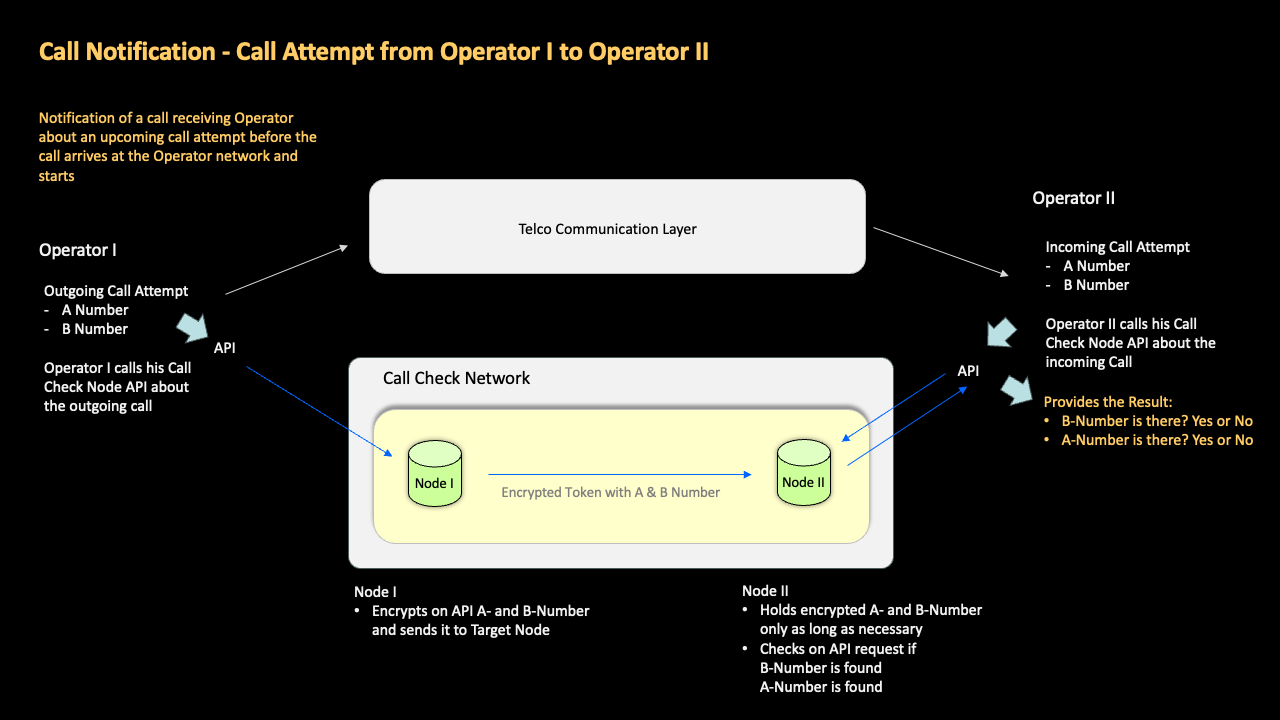
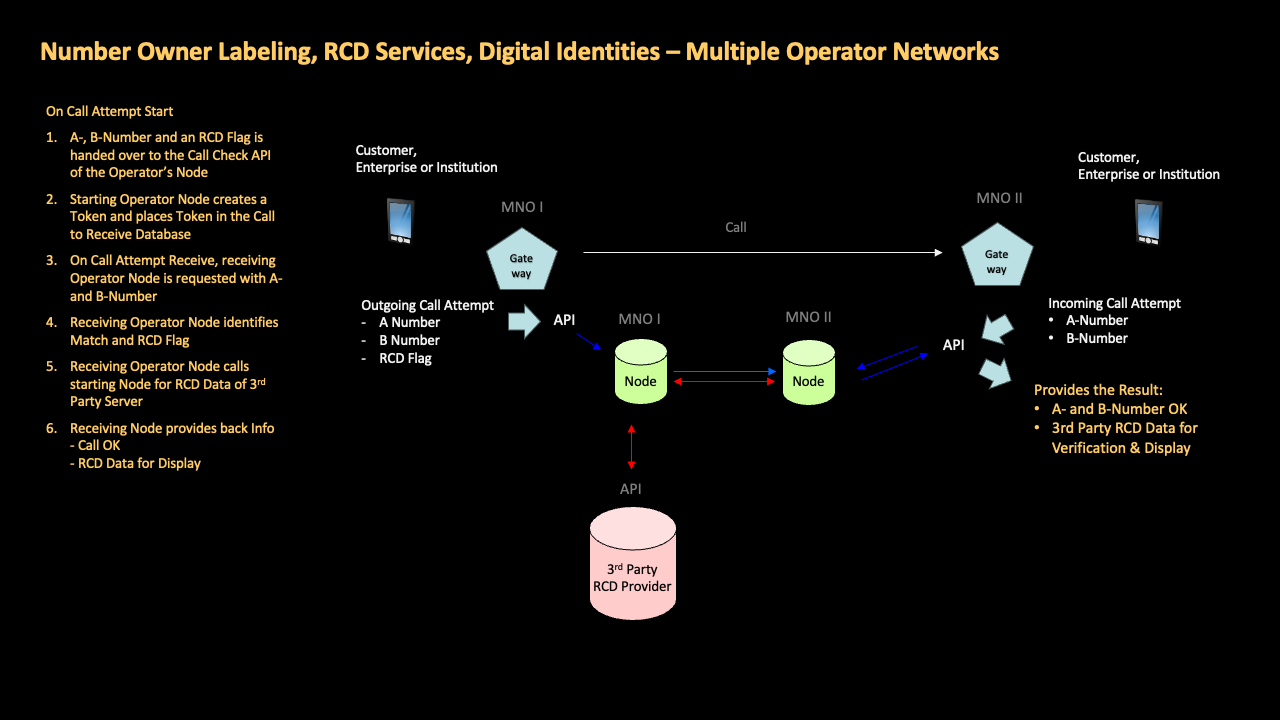
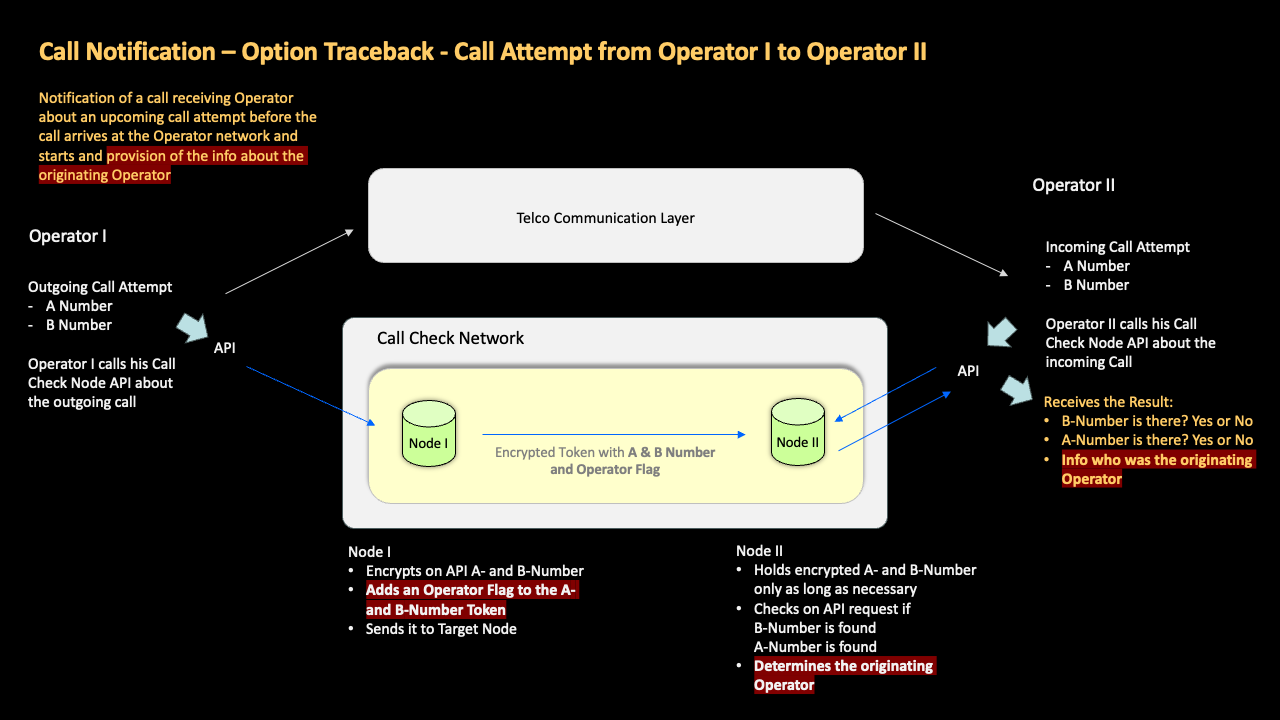
GSMA Call Check lets the receiving telco network know “ahead of call start” that a call is coming, and then automatically performs a comprehensive but fast-acting series of checks to identify calls which are using spoofed numbers, so that operators have an opportunity to block them, and thereby prevent scammers from reaching consumers via the voice network.
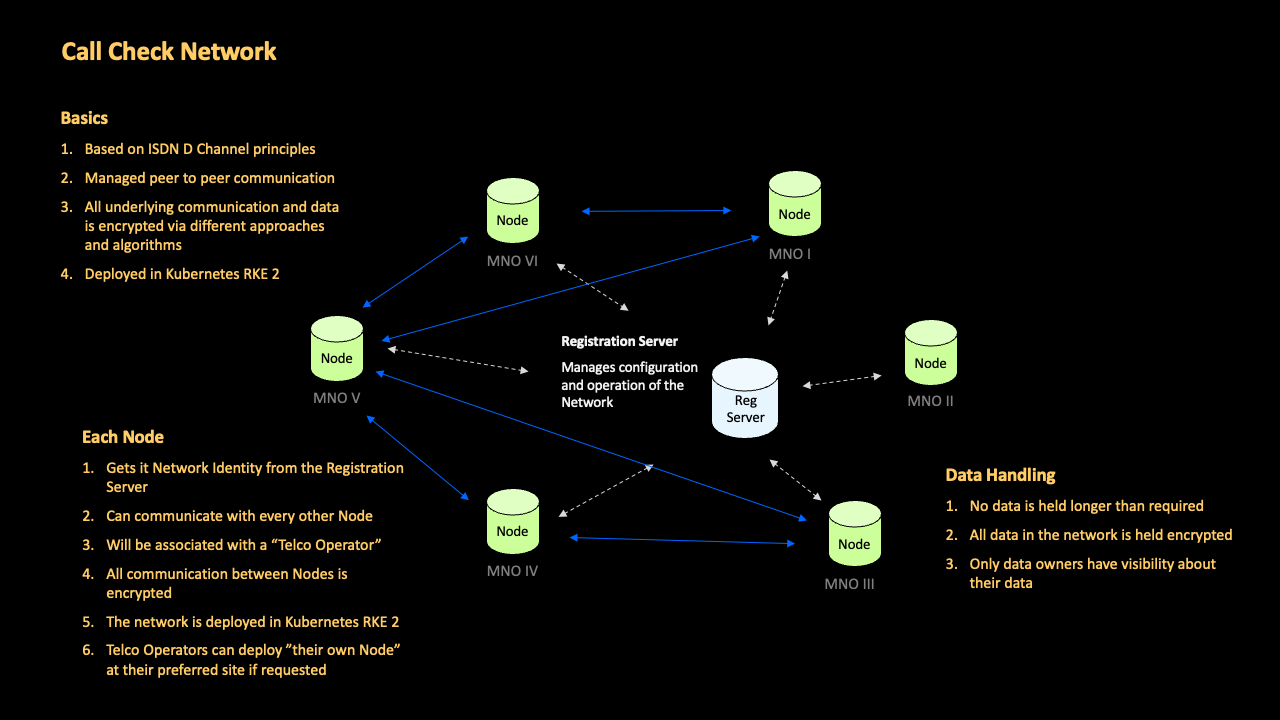
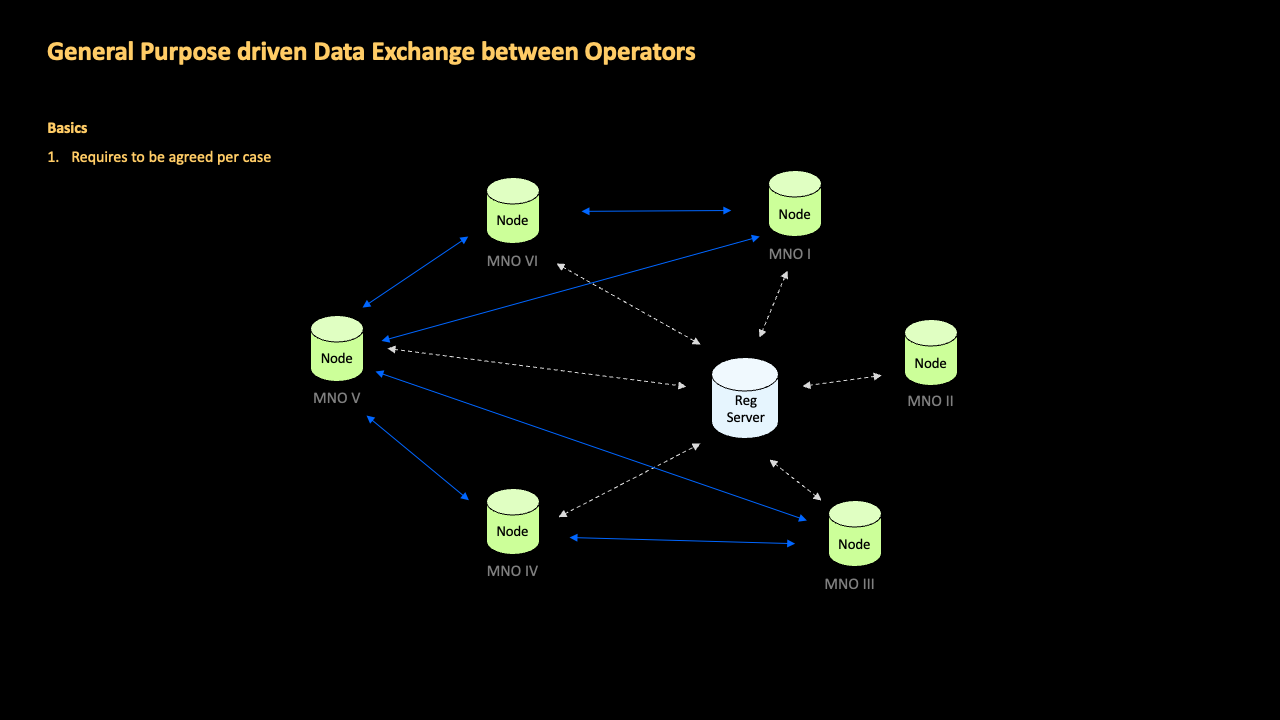
When operators subscribe to the service, they are allocated a dedicated node within the Call Check network. Within the network, node servers communicate with each other based on the configuration managed via the registration server.
All peer-to-peer communications via the network feature end-to-end encryption, whereby the data required during processing operations is encrypted both at-rest and in-transit. In line with GDPR, data is minimized and held only as long as necessary to fulfill the network’s purpose.
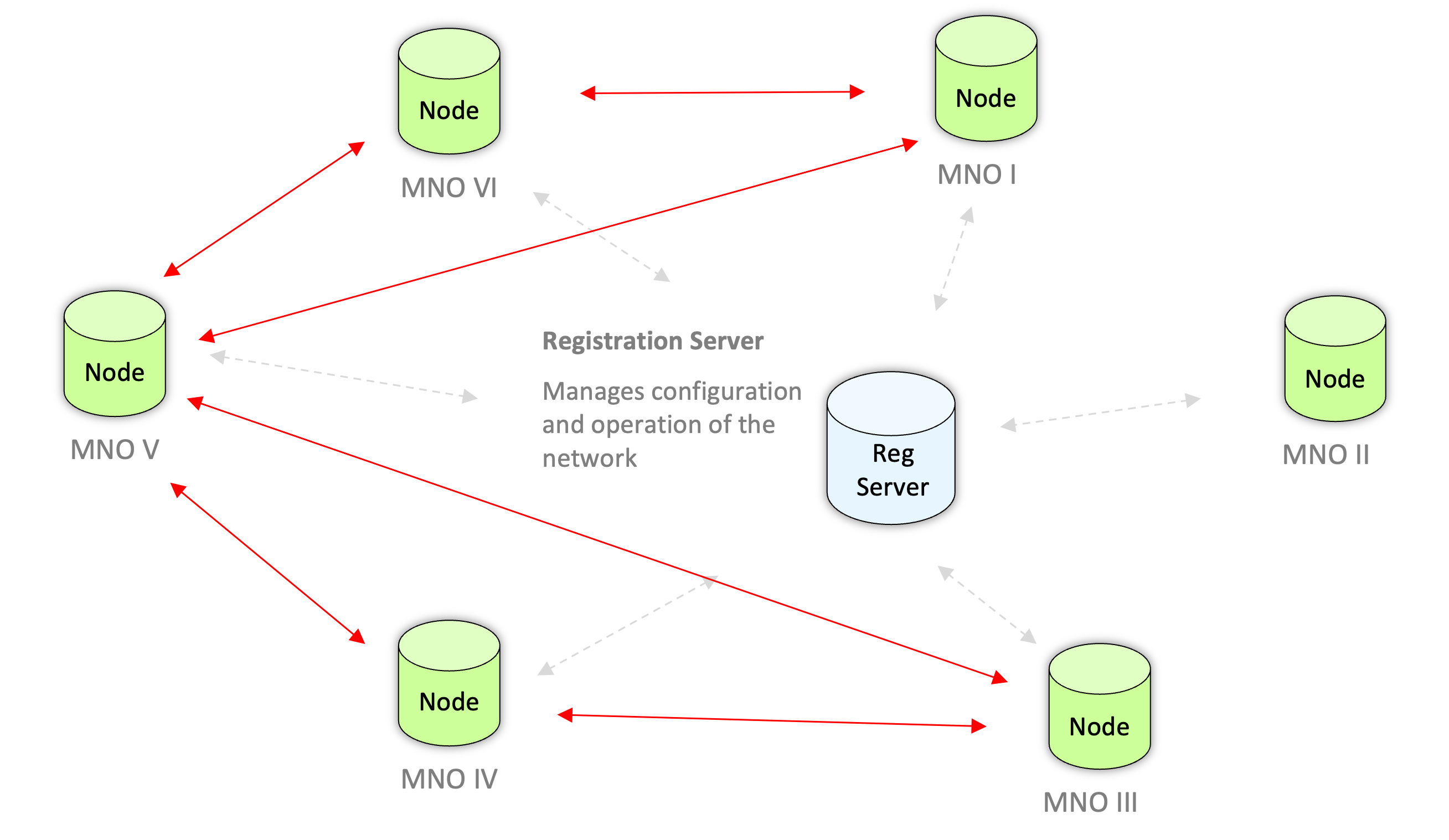
Operators communicate with their network node via API. Therefore, the implementation of GSMA Call Check is extremely light and quick, and for the operator the task of configuring these APIs represents the extent of the technical onboarding.
GSMA Call Check supports a wide range of use cases in the context of enhancing security and fraud resilience of telecom communications and they generally sit within the following two main areas of focus
I. Consumer Protection
II. Commercial Frauds
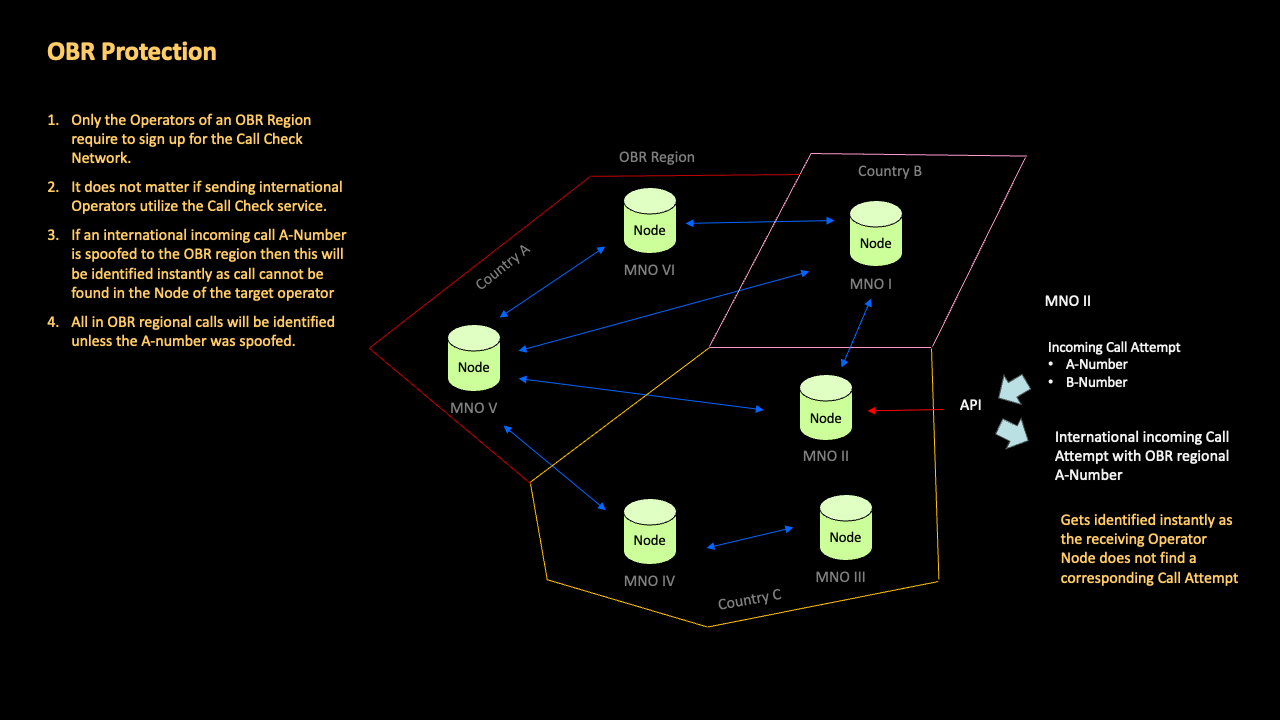
In this use case, nodes inform on call setup the nodes of expected receiving operators about an incoming call attempt in a given country. The node receiving the incoming call check from his owning operator (when the call attempt arrives via the telecoms network) will verify the call attempt while all other nodes, which were notified as well, forget about this notification instantly.
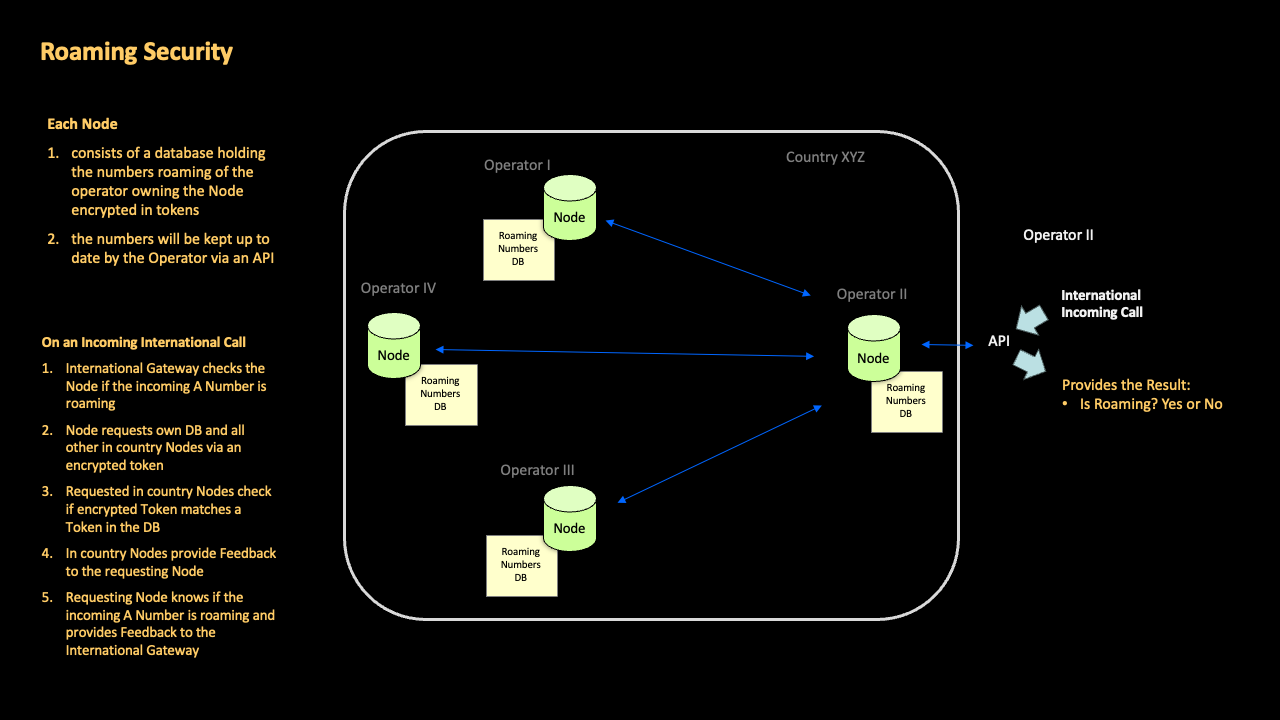
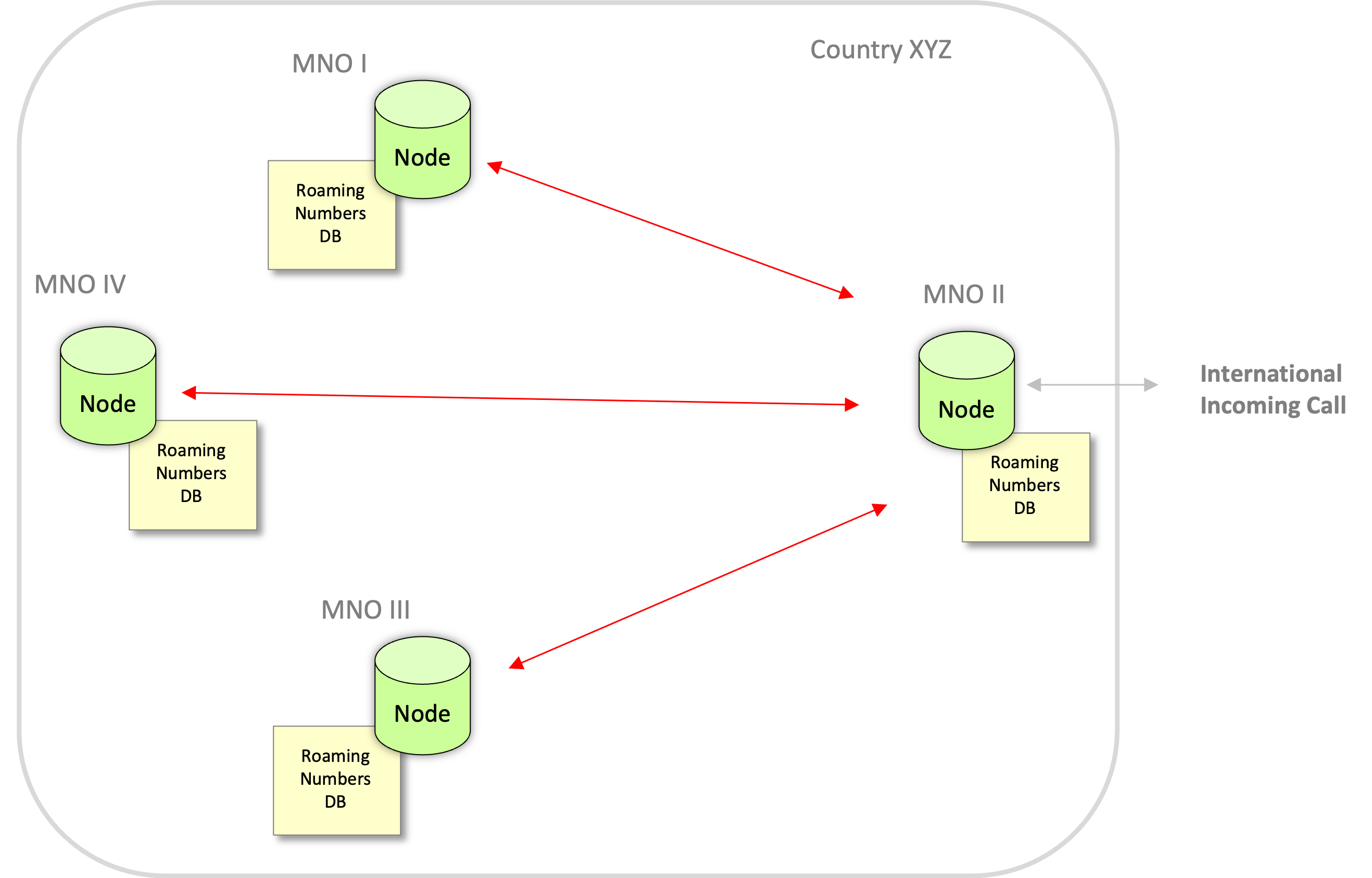
Roaming status checks (and similar legitimate exceptions documented in ECC (23)03) are vital to ensure that calls from outbound roamers do not get falsely blocked.
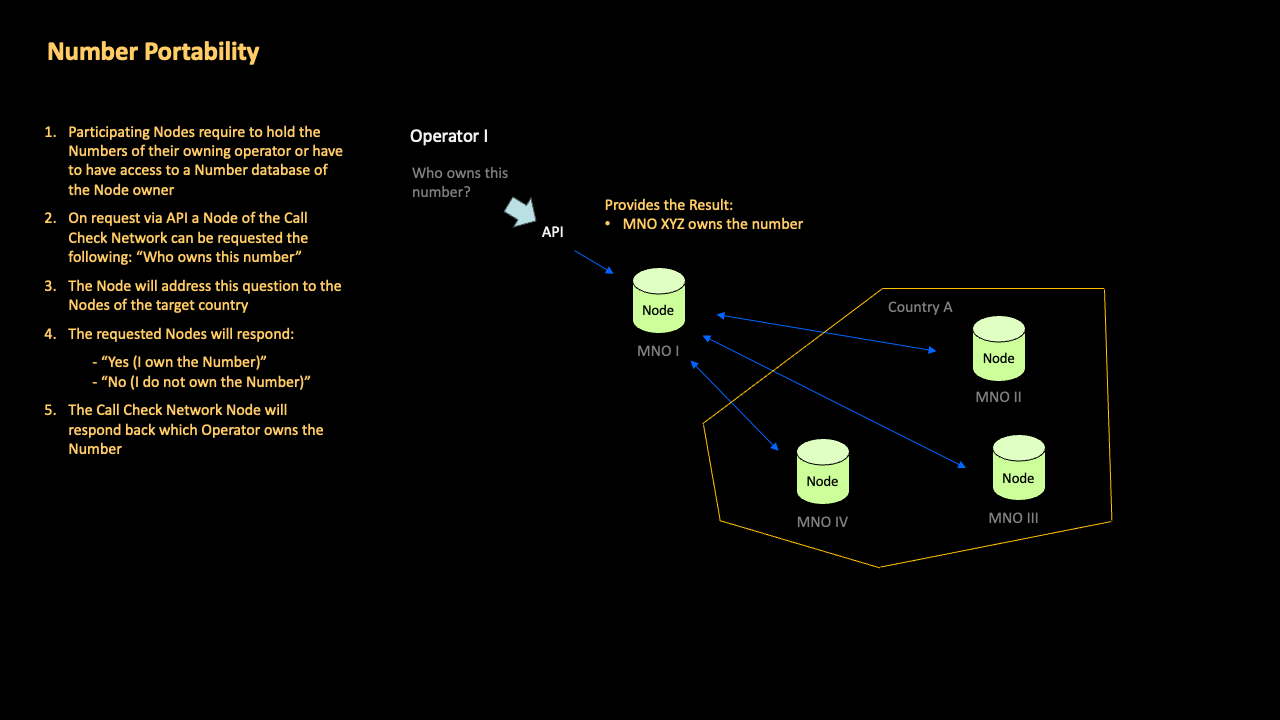
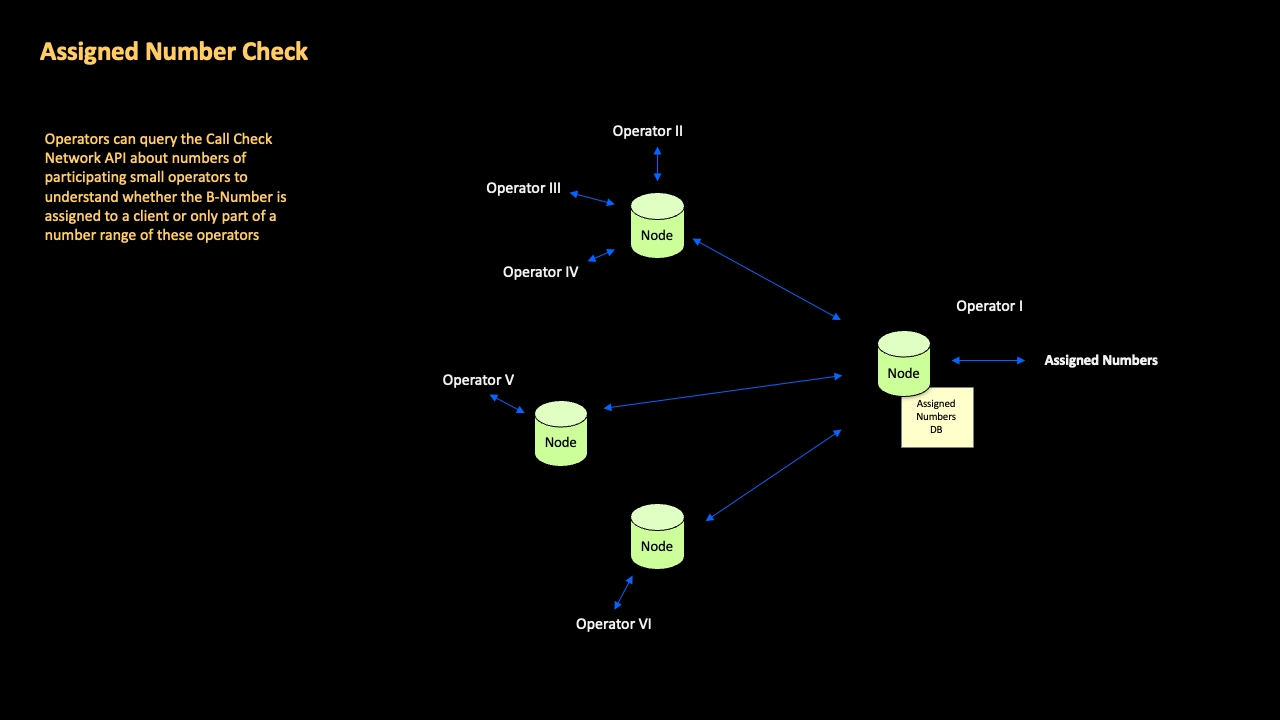
GSMA Call Check directly empowers inter-operator collaboration in a given country, so that each national operator has the ability to instantly verify that an incoming international call with a national A-number belongs to a roamer on any national network, not just their own.
With GSMA Call Check this is done without disclosing commercially-sensitive roaming information to other operators, or centrally storing roaming numbers.
Plenty of other use cases exist and are already on the agenda such as
Operation requires the connection via API or SIP as API alternative. A slim Web client verifies the own node is working.
GSMA Call Check has been rigorously pen tested by two separate and independent leading authorities, in order to ensure the highest levels of system security and data privacy.